METHODS OF ERROR DETECTION |
|
Topics from the Cambridge IGCSE (9-1) Computer Science 0984 syllabus 2023 - 2025
|
OBJECTIVES
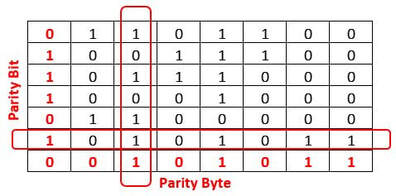
2.2.1 Understand the need to check for errors after data transmission and how these errors can occur 2.2.2 Describe the processes involved in each of the following error detection methods for detecting errors in data after transmission: parity check (odd and even), checksum and echo check. 2.2.3 Describe how a check digit is used to detect errors in data entry and identify examples of when a check digit is used, including international standard book numbers (ISBN) and bar codes 2.2.4 Describe how an automatic repeat query (ARQ) can be used to establish that data is received without error. |